

Blockchain-Based Identity Infrastructure
Replace password-based authentication with cryptographic signatures. Users retain data ownership and reputation portability across the ecosystem.

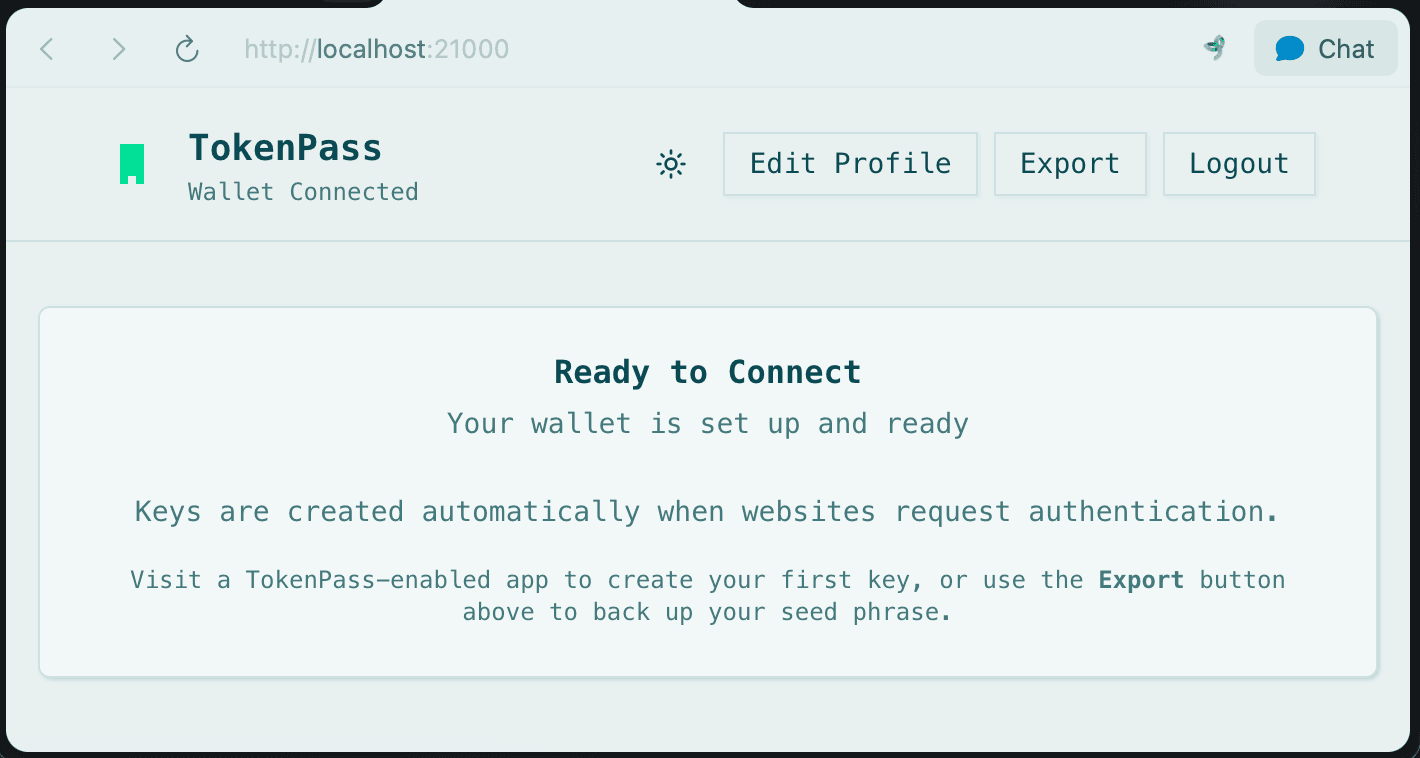
TokenPass Identity Wallet
Personal OAuth System
No cloud accounts, no gatekeepers, same familiar experience.
Privacy-First Identity
Your keys never leave your device. Every operation happens locally using Bitcoin cryptography.
Your Own OAuth Provider
Replace Google, GitHub, and other identity providers. Authenticate to any app with your Bitcoin identity.
Per-App Key Isolation
Each website gets a unique derived key. Apps can't track you across sites or correlate your identities.
The password problem is not going away, so we are moving around it.
Traditional passwords are the original sin of internet security. We store them in databases that get breached and transmit them across networks where they are intercepted. While this system fails humans, the revolution that began with OpenClaw agents proves that autonomous entities need a far more robust solution.
This wave of agentic growth will not stop. As agents become the dominant force in the digital economy, they require identity solutions like Sigma Identity to function as their version of KYC. To operate effectively, these agents need a verified way to use stablecoins, exchange assets among each other, and utilize communication channels while building trust among themselves.
Sigma Identity eliminates passwords entirely. Both humans and agents authenticate by signing cryptographic challenges with their private keys. This is the same technology that secures billions of dollars in Bitcoin. Nothing is stored and nothing is transmitted. Because there is no central database of secrets, there is nothing for a malicious actor to breach.
Four steps to owning your identity
Create Your Identity
Generate a master seed protected by your password. This creates your Bitcoin-backed identity that only you control.
Connect to Apps
When an app requests authentication, TokenPass derives a unique key for that app. No two apps see the same identity.
Sign & Authenticate
Approve signing requests with one click. The app receives cryptographic proof of your identity without seeing your private keys.
Build Your Reputation
Your actions and attestations accumulate across the ecosystem. Switch apps without starting over. Your reputation travels with you.
AI-assisted integration
Install our Claude plugin and let AI guide you through the entire setup process.
$ claude plugins add @sigma-auth/better-auth-pluginAI Integration Agent
The plugin includes an expert agent that understands OAuth flows, token management, and BAP identity integration. Ask it anything.
Guided Setup
Walk through environment variables, callback handlers, and client configuration with contextual help at every step.
Code Generation
Generate auth clients, API routes, and callback pages tailored to your Next.js, React, or vanilla JS setup.
Or install the package directly:
npm install @sigma-auth/better-auth-pluginStandard OAuth. Sovereign infrastructure.
Sigma Identity speaks OAuth 2.0. If your application already supports social login, you can add blockchain-based authentication in an afternoon. Same flow, same endpoints, same redirect patterns—backed by cryptographic proof instead of corporate databases.
Web SDKs
JavaScript libraries for React, Vue, and vanilla JS. TypeScript support built in.
Mobile SDKs
Native iOS and Android libraries. Uses device secure enclaves for hardware-backed key storage.
Enterprise APIs
REST endpoints and SAML bridges for existing identity infrastructure.

